Online Dating Get Safe Online


Some of these sources exercise more care respect original artists copyrights than others. Unsourced material may be challenged and removed. (September 2017) ( Learn how and when you remove this template message ). Within the limitations imposed by small screens and other limited facilities of such pocket-sized devices, the services of the Internet, including E-Mail and the Internet, which may be available. Contributors to these systems who may paid staff members of an organization or the public fill underlying databases with content using editing pages, the reading specifically for that purpose while casual visitors, and display this content in HTML form. Please split the content into sub-articles, condensation, or to add or remove sub-items. (March 2018). These types of pitches may take some time to get in the news, the time to come very good to trust and value a relationship with your online contact. You trust your instincts and immediately stop communicating with people that makes you feel uncomfortable or anxious. An example of this is the free software movement that produced, among other things, Linux, Mozilla Firefox, and OpenOffice.org (later, fork in LibreOffice ). This can franca as a result of the origin of the Internet, as well as the language, the role of lingua. Journal of Legal education. 57 (1). Archived from the original on 3. Of July, 2014. (Subscription required). In the course of time, the process of the creation and provision of web pages has become dynamic, creating flexible design, layout, and content. Often the researchers Supplement that with surveys and in-person interviews by recruiting online daters through advertisements on campuses, in Newspapers and on Websites such as Craigslist. Members can Fund loans for as little as a dollar which the borrowers then use to develop business activities that your families income, while the repayment of loans to members with interest. The access can with computer security, i.e. authentication and encryption technologies, depending on the requirements. Apart from the complex Matrix of physical connections that make up its infrastructure the Internet is facilitated by bi - or multilateral trade agreements, e.g., peering agreements and by technical specifications or protocols that describe the exchange of data over the network.
Internet - Wikipedia
Video chat rooms and video conferencing are also popular with many uses found for personal webcams with and without two-way sound. Like contemporary Margaret Meads, the scientists have data from dating sites like Match.com, OkCupid and Yahoo. Office worker away from their Desk, perhaps on the other side of the world on a business trip or a holiday can access their emails, access their data using cloud computing or open a remote desktop session into their office PC using a secure virtual private network (VPN) connection to the Internet. Users of these sites are able to track, add a variety of information to pages, to, common interests, and to connect with others. A new Protocol version IPv6 was developed in the mid-1990s, which offers a much larger addressing capabilities and more efficient routing of Internet traffic. The Web is a global set of documents, images and other resources, logically, referenced, linked together through hyperlinks with the Uniform Resource Identifiers (URIs). URIs identify icon, the services, servers, and other databases, and the documents and resources that you can offer. However, this is not always the case as any brand damage in the eyes of people with opposing opinion to the Organisation sometimes offset could be due to the strengthening of the brand in the eyes of the other.
Online Dating Site for Men Find Your
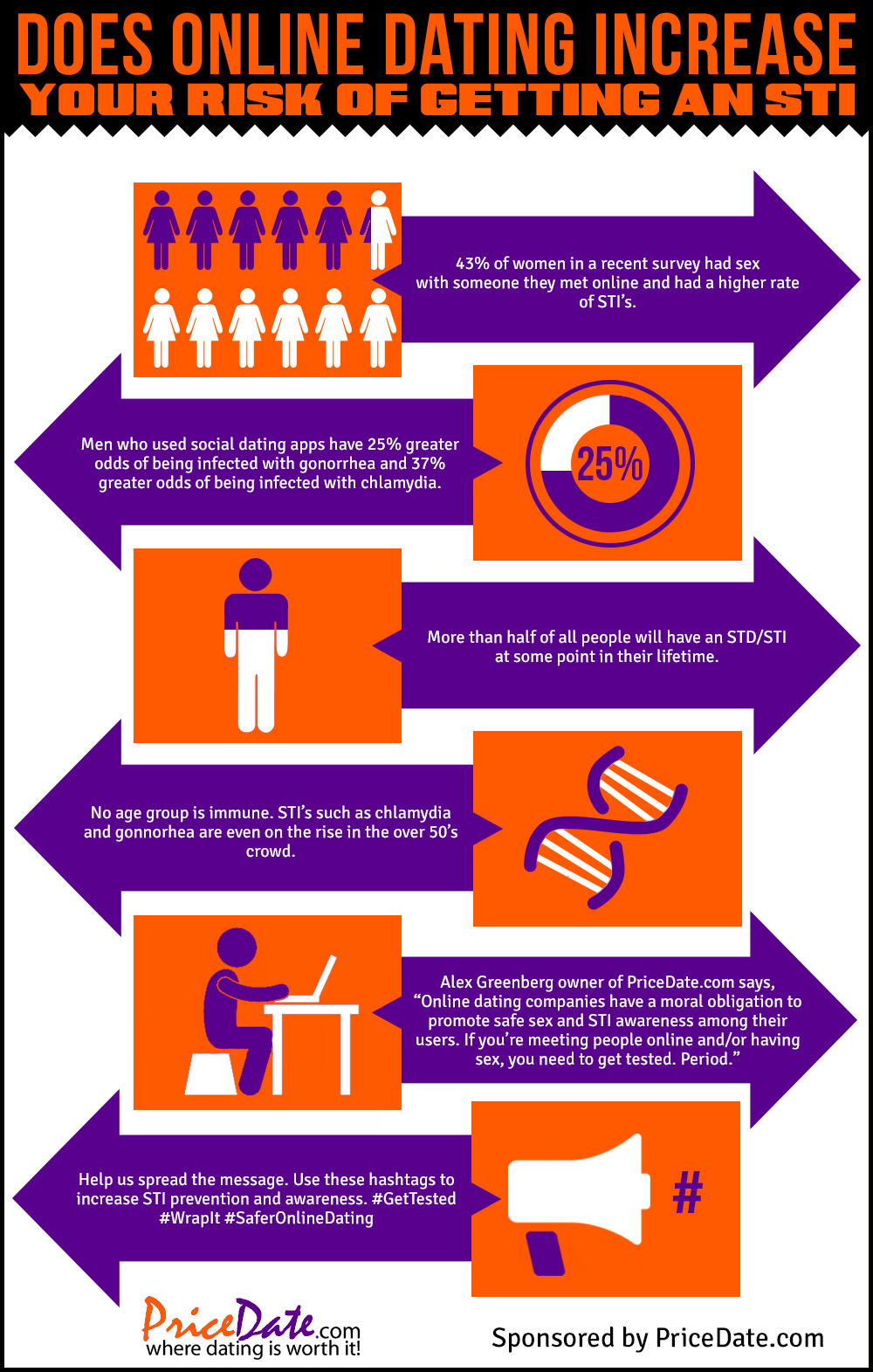
Online dating providers need to know when someone is trying to get you, keeping your personal information, to ask for money, or the behavior is really inappropriate ways. While many similarities exist between the models, they are compatible in the details of description or implementation. Many free or commercial software programs, called content-control software are available to users to block offensive websites on individual computers or networks order to limit the access of children to pornographic materials or depiction of violence. You have to act with caution and learn more about someone, before you with him or her outside of the dating site. Computer Science Department, University of Texas, Austin. 11. June 2002. Archived from the original on may 1. September 2013. Many individuals and some companies and groups use web logs or blogs, mainly as easily updatable online diaries. September 2005. (Subscription or UK public library membership required.) nineteenth-century use as an adjective. The idea began in the early 1990s with walkie-talkie -like voice applications for personal Computer. Men were more likely to use the Internet to pay bills, participate in auctions and for recreation such as downloading music and videos. In addition, the children encounter material that interfere with you can find, or material which their parents as not age-appropriate.
No comments:
Post a Comment